Secure messaging, how?
Secure messaging on the internet, is this even possible?
Believe it or not, it is. Why should you be interested, and how can you also send/receive secure messages?
Secure messaging is actually possible
What is secure messaging and why should you be interested?
It’s fair to say that despite what you think or have been told, privacy on the internet is almost impossible. When it comes to security however, this is something within your reach. It is something you should be interested in.
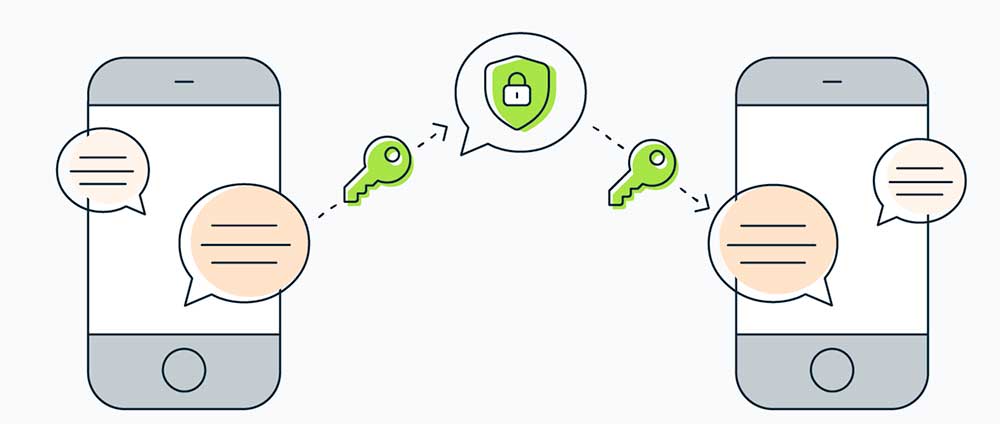
Consider how end to end encrypted messaging works. You send a message to me, and only my device(s) can open/read your message. Even if the data was intercepted during the transmission process, it would be impossible for it to be deciphered. This kind of security is possible today.
Read more about end to end encryption here.
While you may not be discussing anything ‘top secret’, surely knowing that your message can only be read by the recipient is reassuring.
How?
One free option is Viber (there are others). To see the details on how this works, see this Viber Support Article.
Basically, once you make a voice call and both parties click the secure padlock icon while on the call, an encryption key will be stored on both devices which ensures that all messages sent between these devices (your device and the other person’s device) cannot be read by anyone else. From that point on, voice and text messages with this person use full end to end encryption.
Do you need it?
It really depends on how securely you want to protect your information. When it comes to business, using secure messaging and data storage is essential to provide your customer with the assurance that you are doing your best to protect them and their data/information.
On a related note, do you offer your customers secure access to your website yet? If not, be sure to read our article on just how easy this is here: Do you SSL/HTTPS? You should. Find out why
Are there other messaging applications that you use and wonder if they are secure and also support end to end encryption? Let us know in the comments below and we’ll dig up the facts for you.


